After installing the latest iOS 7 updates on several of my Apple products, I discovered a feature that could also provide unintentional insight to users’ accounts.
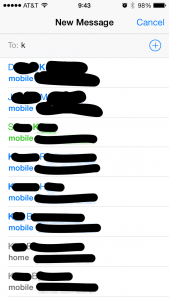
When composing a new iMessage, typing a few letters provides a list of matching entries from the system-wide address book. What I found most interesting was that contacts who set up iMessage with their device’s phone number appeared in blue type – regardless of whether you have previously established iMessage-based communication with that contact. Therefore, this feature provides a “blind iOS discovery” function. While looking through my own contacts, I found that this works for domestic and international numbers, as well as email addresses. Of course most of these email addresses are the contact’s Apple ID address. In the screen capture at left, you’ll also see an entry in green text – this signifies a contact with which I have exchanged SMS-based messages in the past. Non-iMessage-capable numbers with which the user has not exchanged SMS messages are shown in the standard grey text.
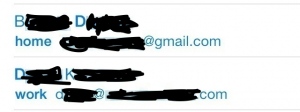
Someone with malicious intent could easily build list of email addresses and phone numbers that iOS users have associated with their Apple account. Such a list of verified iOS phones and Apple ID accounts would be very useful in creating credible phishing texts and emails that aim to compromise their targets’ Apple accounts. (As soon as possible, I will try automating this process as an experiment, and will update this post with results.) While not the most severe example of data leakage, the large number of iOS users is certainly an attractive target for criminals. If nothing else, this is another example of why human vigilance is so important in the face of electronic threats.